A new venture for digital transformation
Riyadh- June 19, 2022 – Aramco and Cognite, a global leader in industrial software, have launched CNTXT, a joint venture based in the Kingdom of Saudi Arabia. Headquartered in Riyadh, CNTXT will support the Kingdom’s industrial digitalization, and the wider MENA region.
CNTXT will provide digital transformation services enabled by advanced cloud solutions and leading industrial software. These solutions and services will help companies in the public and private sector future-proof their data infrastructure, increase revenue, cut costs and reduce risks while enhancing operational sustainability and security.
Google Cloud’s exclusive reseller in KSA
CNTXT is Google Cloud’s reseller for cloud solutions in the Kingdom and the exclusive reseller of Cognite Data Fusion in the MENA region. Additionally, Google Cloud is expected to launch a “Center of Excellence” later this year to provide training to developers and business leaders in how to use cloud technologies.
Leadership and growth plans
Led by Abdullah Jarwan, appointed CEO of CNTXT, and a management team of local and international talent, CNTXT plans to significantly grow the team this year in hopes to become the top tech employer in the Kingdom.
The launch of CNTXT is a major milestone in the collaboration between Aramco and Aker ASA, the majority owner of Cognite. The partnership began in 2019, with the signing of a Memorandum of Understanding (MoU) to develop synergies and share knowledge on industrial digitalization and sustainability initiatives.
The future with CNTXT
Ahmad A. Al-Sa’adi, Aramco Senior Vice President, Technical Services, said: ‘’CNTXT brings together industrial legacy, unmatched technology, and a truly talented team that will aid in the digitalization of public and private sectors in the Kingdom. CNTXT will be an important catalyst of digitalization of the Kingdom.”
Øyvind Eriksen, President of Aker ASA and Chair of the Cognite Board of Directors, said: “CNTXT will be an important vehicle for driving profitability and sustainability of the Kingdom’s industries through innovative use of technology. I look forward to seeing the company accelerate the digital transformation of the most important sectors in the region.”
“The untapped potential in the digital transformation of the Kingdom of Saudi Arabia and the greater Middle East is enormous. With Google Cloud and Cognite offerings in our portfolio, we can help the public and private sectors innovate faster, scale AI-driven solutions, and turn data into value.” Said Abdullah Jarwan, CEO of CNTXT.“Businesses all around the world turn to Google Cloud to enable growth and help them solve their most business-critical challenges. With CNTXT as Google Cloud’s reseller in the Kingdom, we will be leveraging the latest technologies and decades of expertise to help businesses grow and develop safely and securely,” said AbdulRahman Al Thehaiban, Managing Director, Middle East, Turkey and Africa, Google Cloud.
Why the cloud?
Cloud computing is a technology model that disrupts how traditional IT infrastructure and services work. It is based on 5 main pillars that unlock the highest potential for its users, in the form of greater efficiency, resilience, agility and scalability.
The five pillars of cloud
Pillar #1: Shared resources
Cloud computing operates through a set of data centers that are managed by a third party, known as the cloud provider. The cloud provider offers a shared pool of IT resources, including networks, servers, storage, services and applications.
Pillar #2: Scaling on-demand
The shared resources are offered and provisioned to customers based on needs. This means cloud users can scale their infrastructure or service capacity rapidly with minimal effort to meet specific peak seasons to accommodate increased demands. Unlike traditional IT setups, this will save massive time spent on procuring and configuring additional resources and services.
Pillar #3: Self provisioning
Cloud is designed to be simple and accessible for its users. Users can access additional resources or services seamlessly without needing to wait for the cloud provider.
Pillar #4: Pay-as-you-go
The cloud revolves around efficiency and resource optimization. In a clear departure from traditional models, it measures every resource the customer uses and only charges per consumption. This pay-as-you-go approach allows users to keep a tab on their consumption and optimize their resource allocation, ensuring maximum return on investment.
Pillar #5: Universal access
Users can access their resources and services anytime, from anywhere. But you will need to configure your cloud to prevent unauthorized access. This leads us to a critical aspect of cloud computing—security.
Cloud and cybersecurity go hand in hand
Migrating to the cloud has changed how customers and businesses store and access their data. Gone are the days when everything had to be stored and managed only from one place. With advancements in cloud service delivery offerings, users can adopt the cloud in various models that better suit their business needs and organization’s risk profile.
The main models are private cloud, public cloud and hybrid cloud. You can refer to this page for a detailed definition of these models by our strategic partner, Google Cloud.
As organizations move to the cloud, getting cyber-savvy is crucial to ensure you limit any potential exposure. In fact, cybersecurity has become a competitive edge among the leading cloud providers, all of which are making continuous investments in cybersecurity to increase the robustness and resilience of their cloud solutions.
Your cybersecurity blueprint for the cloud
New to the cloud? The following 9-step blueprint is designed to bolster your cloud security and ensure your data remains protected.
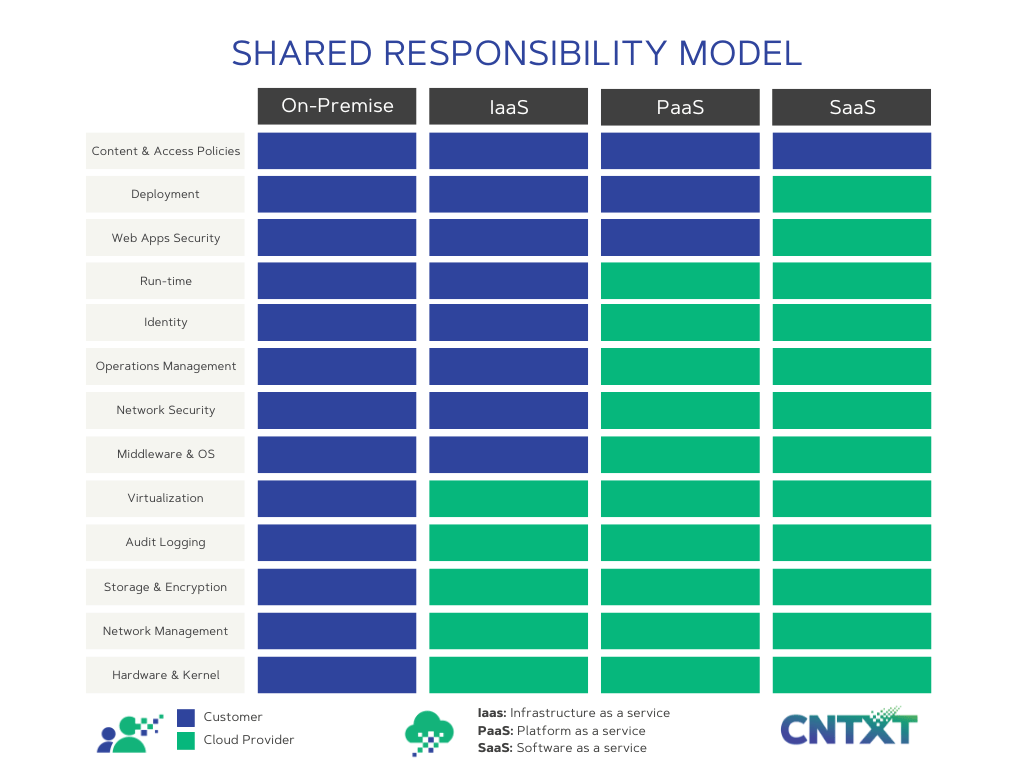
- Know what you’re responsible for. Cybersecurity for the cloud is a “shared responsibility model.” You need to understand which security responsibilities will be delegated to the cloud provider and which will remain with your organization’s users and security team. Check out the illustration for a quick guide.
- Utilize the tools available on the cloud to provide logical isolation among critical resources and services.
- Classify your data before hosting on the cloud and enable data protection tools and features to provide an additional security layer to your sensitive data (e.g., data leakage prevention, external encryption key manager).
- Manage identities and authorizations carefully for regular and privileged cloud users to maintain good hygiene.
- Utilize cloud tools or external solutions to securely store and manage encryption keys, passwords, certificates and other sensitive information.
- Always harden and review any default settings and configurations of the cloud resources to ensure it complies with your organization’s policies or applicable regulatory requirements.
- Enable two-factor authentication for accessing cloud services.
- Periodically scan and monitor the workload on the cloud to uncover any weaknesses, vulnerabilities or mis-configurations.
- Configure and set security alerts on the cloud platform and services to ensure timely notification and automated action, where applicable, on suspicious activities.
Reach out to our cybersecurity experts
Stay abreast of how you can keep your organization cloud-secure by checking out the free resources offered through Google Cloud security best practices center. Want to talk to an expert? Our cybersecurity team will be happy to assist you at [email protected].
Augment, Democratize, Consumerize
The 2020s have been eventful for enterprises in the Kingdom of Saudi Arabia and the Middle East. Even the most conservative tech adopters were forced to take a digital leap that would have been unimaginable in the pre-pandemic era, and the results of the global digital-by-necessity experiment so far have been staggering.
Much has been written about tech in the workplace so, for this article, we are focusing on a very specific field of technology: industrial data management. More specifically, we are zooming in on how cloud data storage will finally be connected to industrial use-case solving at scale, unlocked by advances in that elusive-yet-critical “hidden layer” between data storage and application logic.
These are not more vague predictions about digital twins. In fact, we expect three bigger themes to dominate the sector this year:
- Augmentation – the process of enhancing or amplifying existing capabilities.
- Democratization – the widespread accessibility of data-driven insights to non-specialist users.
- Consumerization – ease of use, patterned after consumer applications.
These prevailing themes—augmentation, democratization and consumerization—are the foundation for industry 2.0. With that in mind, let’s explore the four significant trends that stand to redefine the data management landscape in the next couple of years.
1: A new era of data governance
First on our list, traditional corporate data governance will give way to a more democratized, ambient approach. Organizations will need to tailor their data governance strategies to suit different types of data and analytics, shifting from a centralized, use-case-agnostic practice to one that is deeply tied to the needs of actual data consumers and their data-driven use cases.
Through this paradigm shift, data governance—and master data management—will become a facilitator, rather than a hindrance, to faster use case execution and greater team autonomy. As a first step, we predict that data discovery will become an indistinguishable part of data governance.
2: Through AI, industrial data will learn to speak human
AI-driven active metadata creation permeates industrial data management, shifting the emphasis from data storage and cataloging to a true human data discovery experience. For application developers and data scientists, understanding—and handling—industrial data is not as straightforward as dealing with tabular data.
What’s even harder is understanding the context of industrial data—especially if you’re not a subject matter expert with years of intimate experience with the asset. Now, with AI making a steady march through industry, we expect to see technologies such as NLP, OCR, computer vision, trained ontologies and graph data models used to automatically contextualize ET/OT/IT, so the data is available for intuitive human use as well as programmatic discovery and analysis.
3. Enterprises will invest more in metadata (and its management) than in data (and its management) itself
When a data lake is not properly controlled, it becomes a data swamp . Currently, too many data science teams are scrambling to convert the contents of their data warehouses and data lakes into business value.
To meet the market’s growing need for human-understandable data, the role of metadata management is stepping up. This change is driven by the expansion of the Chief Data Officer’s mandate, which now includes metadata ownership, a responsibility previously held by the CIO.
4: DataOps will connect data managers to data consumers in real-time, at unprecedented scale
Data operations—DataOps—is collaborative data management for the AI era. The convergence of data management with data analytics continues to accelerate, driven by a surge in data literacy among data users. Seamless data operationalization across all workflow steps, ranging from data sources to live applications, becomes the new ‘data trapped in source system siloes’ challenge for digital and innovation leaders.
Stay ahead of the trend curve
CNTXT is your digital transformation partner in the MENA region. Through leading Google Cloud solutions, industrial software and digital know-how, we empower you to act on the industrial data trends to maximize your enterprise’s competitive advantage.
CNTXT can help you future-proof your data infrastructure, enabling you to contextualize your data so it’s ready for numerous AI applications and to capture the insights you need.
Together, we can unlock your enterprise’s limitless capacity for growth through digital transformation and data-driven insights. To book a consultation, please contact us.
