Why the cloud?
Cloud computing is a technology model that disrupts how traditional IT infrastructure and services work. It is based on 5 main pillars that unlock the highest potential for its users, in the form of greater efficiency, resilience, agility and scalability.
The five pillars of cloud
Pillar #1: Shared resources
Cloud computing operates through a set of data centers that are managed by a third party, known as the cloud provider. The cloud provider offers a shared pool of IT resources, including networks, servers, storage, services and applications.
Pillar #2: Scaling on-demand
The shared resources are offered and provisioned to customers based on needs. This means cloud users can scale their infrastructure or service capacity rapidly with minimal effort to meet specific peak seasons to accommodate increased demands. Unlike traditional IT setups, this will save massive time spent on procuring and configuring additional resources and services.
Pillar #3: Self provisioning
Cloud is designed to be simple and accessible for its users. Users can access additional resources or services seamlessly without needing to wait for the cloud provider.
Pillar #4: Pay-as-you-go
The cloud revolves around efficiency and resource optimization. In a clear departure from traditional models, it measures every resource the customer uses and only charges per consumption. This pay-as-you-go approach allows users to keep a tab on their consumption and optimize their resource allocation, ensuring maximum return on investment.
Pillar #5: Universal access
Users can access their resources and services anytime, from anywhere. But you will need to configure your cloud to prevent unauthorized access. This leads us to a critical aspect of cloud computing—security.
Cloud and cybersecurity go hand in hand
Migrating to the cloud has changed how customers and businesses store and access their data. Gone are the days when everything had to be stored and managed only from one place. With advancements in cloud service delivery offerings, users can adopt the cloud in various models that better suit their business needs and organization’s risk profile.
The main models are private cloud, public cloud and hybrid cloud. You can refer to this page for a detailed definition of these models by our strategic partner, Google Cloud.
As organizations move to the cloud, getting cyber-savvy is crucial to ensure you limit any potential exposure. In fact, cybersecurity has become a competitive edge among the leading cloud providers, all of which are making continuous investments in cybersecurity to increase the robustness and resilience of their cloud solutions.
Your cybersecurity blueprint for the cloud
New to the cloud? The following 9-step blueprint is designed to bolster your cloud security and ensure your data remains protected.
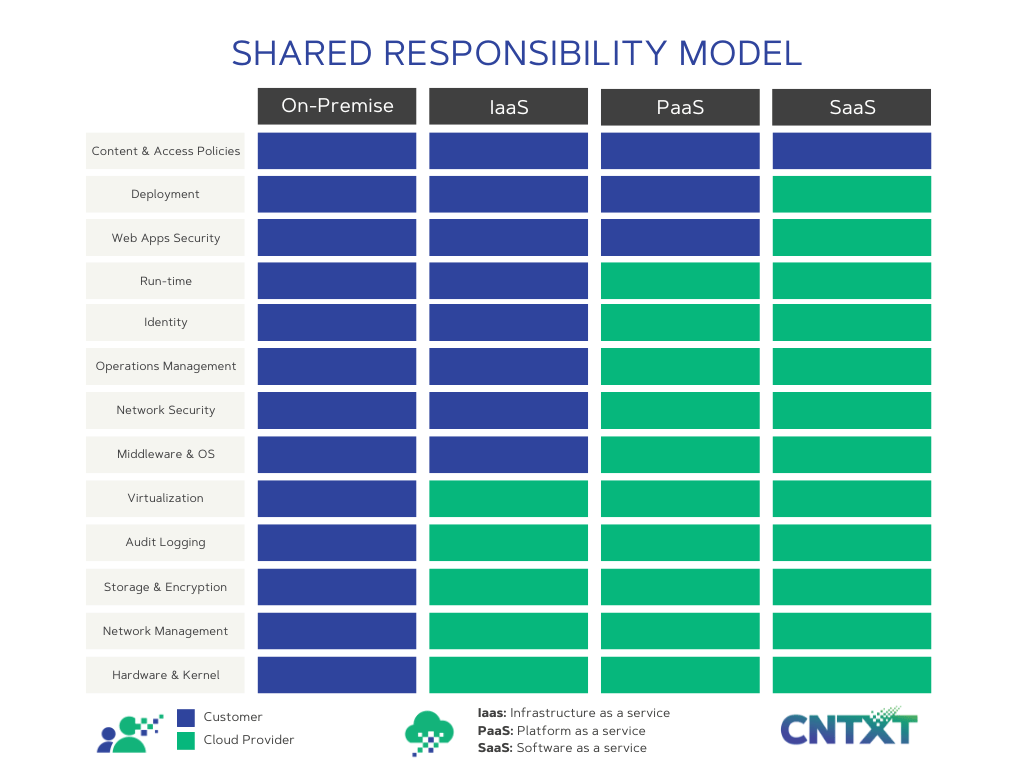
- Know what you’re responsible for. Cybersecurity for the cloud is a “shared responsibility model.” You need to understand which security responsibilities will be delegated to the cloud provider and which will remain with your organization’s users and security team. Check out the illustration for a quick guide.
- Utilize the tools available on the cloud to provide logical isolation among critical resources and services.
- Classify your data before hosting on the cloud and enable data protection tools and features to provide an additional security layer to your sensitive data (e.g., data leakage prevention, external encryption key manager).
- Manage identities and authorizations carefully for regular and privileged cloud users to maintain good hygiene.
- Utilize cloud tools or external solutions to securely store and manage encryption keys, passwords, certificates and other sensitive information.
- Always harden and review any default settings and configurations of the cloud resources to ensure it complies with your organization’s policies or applicable regulatory requirements.
- Enable two-factor authentication for accessing cloud services.
- Periodically scan and monitor the workload on the cloud to uncover any weaknesses, vulnerabilities or mis-configurations.
- Configure and set security alerts on the cloud platform and services to ensure timely notification and automated action, where applicable, on suspicious activities.
Reach out to our cybersecurity experts
Stay abreast of how you can keep your organization cloud-secure by checking out the free resources offered through Google Cloud security best practices center. Want to talk to an expert? Our cybersecurity team will be happy to assist you at [email protected].
Related Resources
All ResourcesGet in touch
There are many ways of “doing cloud” but not all of them will future-proof your business. We can devise an approach that will. Talk to us today – you have nothing to lose but the guesswork.
Contact Us


